Kubernetes 基本架構
kubernetes 架構介紹
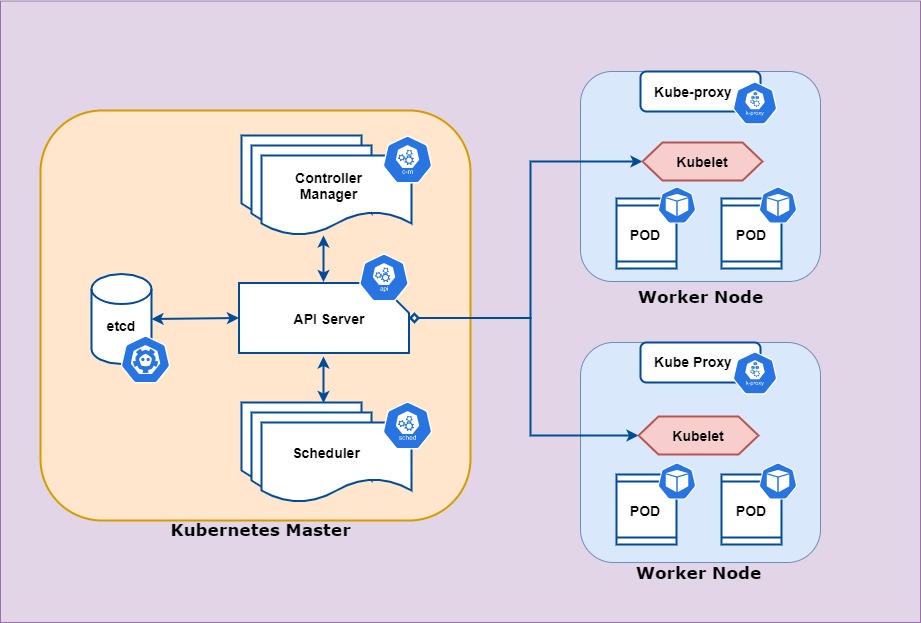 )
)
如果把 K8S cluster 想像成是一間公司,那
Node像是辦公室,作為放置 Pod 的地方Pod像是員工,為最基本的單位Container像是員工的技能,一個 Pod 可以有多個 ContainerMaster Node像是公司總部管理公司資源的調度Worker Node像是分公司,Pod 實際執行運作的地方
| Kubernetes Master | 功能 |
|---|---|
| API Server | 集群中各個節點的溝通橋樑,也負責 K8s 中的請求的身份認證與授權 |
| kube-scheduler | 負責集群的資源調配,調度 Pod 運行在哪個 Node 上,是整個 Kubernetes 集群的調度員 |
| kube-controller-manager | 負責管理並運行 K8s controller 的組件,負責監視 Cluster 狀態的組件 |
| ETCD | 用來存放 K8s Cluster 的資料作為備份,想像為整個集群的 database,記錄整個集群的狀態及資料 |
| Worker Node | 功能 |
| kubelet | 在 Worker node 上對應 api-server 的接口,負責Pod對應的容器的建立、啟動或停止 |
| kube-proxy | 負責維護 Node 上的網路規則,這些規則允許從群集內部或外部的與 Pod 進行通訊 |
| Container Runtime | Node 上運行容器的執行程式,預設是 Docker |
| Pod |
Kubernetes 元件完整介紹
Node 節點
在 Kubernetes 中,Node 通常是指實體機、虛擬機。一個 Node,可以是指 AWS 的一台EC2 或 GCP 上的一台 computer engine ,也可以是你的筆電,甚至是一台 Raspberry Pi。只要他們上面裝有 Docker Engine ,足以跑起 Pod,就可以被加入 Kubernetes Cluster。
Pod
容器化應用程式會在 Pod 中執行。Pod 可包含一個或多個容器,對 Kubernetes 叢集中的應用程式而言,Pod 為最小部署單位。
Pod 可封裝一個 (或多個) 應用程式容器,為 Kubernetes 應用程式中最基本的執行單位。每個 Pod 都包含執行所必備的程式碼和儲存資源,且具有專屬的 IP 位址。Pod 也含有設定選項。通常,Pod 會涵蓋單一容器,或是耦合為單一應用程式或業務功能,且共用一組資源和資料的數個容器。
kube-apiserver
這個 API 伺服器會公開做為通訊中心使用的 Kubernetes API。透過指令行介面 (CLI) 或其他使用者介面 (UI) 進行的外部通訊會傳遞至 kube-apiserver,而所有控制平台至節點的通訊,也會經由 API 伺服器傳遞。
etcd
這個索引鍵值用來儲存與叢集相關的所有資料。etcd 會保持高度可用且一致,原因在於,對 etcd 進行的所有存取,都會透過 API 伺服器進行。etcd 中的資訊通常會格式化為可人工判讀的 YAML 。
kube-schedule
新的 Pod 建立完成後,這個元件會將其指派至節點,以依據資源需求、原則,以及「相似性」規格 (攸關地理區域以及對其他工作負載造成的干擾) 來執行。
kube-controller-manager
雖然 Kubernetes 叢集具有多項控制器功能,這些功能全都會編譯成名為「kube-controller-manager」的單一二進位檔
- 複寫控制器:確保在叢集中執行的每個複寫 Pod,皆存在著數量正確的 Pod
- 節點控制器:監控每個節點的運作狀況,並在節點上線或沒有回應時,向叢集發出通知
- 端點控制器:連接 Pod 和服務,以填入端點物件
- 服務��帳戶和權杖控制器:為叢集中的新命名空間配置 API 存取權杖和預設帳戶
- cloud-controller-manager:如果叢集為部分雲端或全雲端式,雲端控制器管理工具就會將叢集連結至雲端供應商的 API。屆時,只會執行這些雲端供應商專屬的控制器。全地端式叢集上,將不會存在雲端控制器管理工具。叢集內可執行一個以上的雲端控制器管理工具,以做為容錯之用,或用來改善整體雲端效能。
雲端控制器管理工具會包含下列項目:
- 節點控制器:判斷停止回應的雲端式節點狀態,例如是否已遭到刪除
- 路由控制器:在雲端供應商基礎架構中建立路由
- 服務控制器:管理雲端供應商的負載平衡器
kubelet
每個節點都具備名為「kubelet」的代理程式,可用來確保 PodSpecs 中描述的容器能適當運作。
kube-proxy
這是每個節點上的網路 Proxy,會負責維護網路節點,以使用作業系統 (OS) 封包篩選 (若有),進行 Pod 至網路工作階段的通訊,無論於叢集內部或外部。
Container runtime 容器執行階段
負責執行容器化應用程式的軟體。雖然 Docker 最廣為使用,但 Kubernetes 可支援任何符合 Kubernetes 容器執行階段介面 (CRI) 的執行階段。
Deployment 部署
用來部署容器化應用程式 Pod 的方法。部署中描述的目標狀態,將導致控制器變更叢集的實際狀態,進而循序漸進地達到該目標狀態。深入瞭解 Kubernetes 部署。
ReplicaSet
確保在任何指定的時間點,會執行指定數量的相同 Pod。
叢集 DNS
提供必要的網域名稱系統 (DNS) 記錄,以操作 Kubernetes 服務。
容器資源監控
在中央資料庫內擷取和記錄容器指標。
倉管中心
容器映像會保存在倉管中心內,並由控制平台傳輸至節點,以便在容器 Pod 中執行。
目錄結構
/etc/kubernetes
├── main.tf
└── vpc
├── admin.conf
├── controller-manager.conf
├── kubelet.conf
├── scheduler.conf
├── manifests
├── etcd.yaml
├── kube-apiserver.yaml
├── kube-controller-manager.yaml
└── kube-scheduler.yaml
├── pki
├── apiserver-etcd-client.crt
├── apiserver-kubelet-client.key
├── ca.crt
├── ca.key
├── front-proxy-ca.crt
├── front-proxy-ca.key
├── front-proxy-client.crt
├── front-proxy-client.key
├── apiserver.crt
├── apiserver.key
├── apiserver-kubelet-client.crt
├── apiserver-etcd-client.key
├── sa.key
├── sa.pub
└── etcd
etcd
apiVersion: v1
kind: Pod
metadata:
annotations:
kubeadm.kubernetes.io/etcd.advertise-client-urls: https://10.0.1.28:2379
creationTimestamp: null
labels:
component: etcd
tier: control-plane
name: etcd
namespace: kube-system
spec:
containers:
- command:
- etcd
- --advertise-client-urls=https://10.0.1.28:2379
- --cert-file=/etc/kubernetes/pki/etcd/server.crt
- --client-cert-auth=true
- --data-dir=/var/lib/etcd
- --experimental-initial-corrupt-check=true
- --experimental-watch-progress-notify-interval=5s
- --initial-advertise-peer-urls=https://10.0.1.28:2380
- --initial-cluster=k8s-msr-1=https://10.0.1.28:2380
- --key-file=/etc/kubernetes/pki/etcd/server.key
- --listen-client-urls=https://127.0.0.1:2379,https://10.0.1.28:2379
- --listen-metrics-urls=http://127.0.0.1:2381
- --listen-peer-urls=https://10.0.1.28:2380
- --name=k8s-msr-1
- --peer-cert-file=/etc/kubernetes/pki/etcd/peer.crt
- --peer-client-cert-auth=true
- --peer-key-file=/etc/kubernetes/pki/etcd/peer.key
- --peer-trusted-ca-file=/etc/kubernetes/pki/etcd/ca.crt
- --snapshot-count=10000
- --trusted-ca-file=/etc/kubernetes/pki/etcd/ca.crt
image: registry.k8s.io/etcd:3.5.9-0
imagePullPolicy: IfNotPresent
livenessProbe:
failureThreshold: 8
httpGet:
host: 127.0.0.1
path: /health?exclude=NOSPACE&serializable=true
port: 2381
kube-apiserver.yaml
apiVersion: v1
kind: Pod
metadata:
annotations:
kubeadm.kubernetes.io/kube-apiserver.advertise-address.endpoint: 10.0.1.28:6443
creationTimestamp: null
labels:
component: kube-apiserver
tier: control-plane
name: kube-apiserver
namespace: kube-system
spec:
containers:
- command:
- kube-apiserver
- --advertise-address=10.0.1.28
- --allow-privileged=true
- --authorization-mode=Node,RBAC
- --client-ca-file=/etc/kubernetes/pki/ca.crt
- --enable-admission-plugins=NodeRestriction
- --enable-bootstrap-token-auth=true
- --etcd-cafile=/etc/kubernetes/pki/etcd/ca.crt
- --etcd-certfile=/etc/kubernetes/pki/apiserver-etcd-client.crt
- --etcd-keyfile=/etc/kubernetes/pki/apiserver-etcd-client.key
- --etcd-servers=https://127.0.0.1:2379
- --kubelet-client-certificate=/etc/kubernetes/pki/apiserver-kubelet-client.crt
- --kubelet-client-key=/etc/kubernetes/pki/apiserver-kubelet-client.key
- --kubelet-preferred-address-types=InternalIP,ExternalIP,Hostname
- --proxy-client-cert-file=/etc/kubernetes/pki/front-proxy-client.crt
- --proxy-client-key-file=/etc/kubernetes/pki/front-proxy-client.key
- --requestheader-allowed-names=front-proxy-client
- --requestheader-client-ca-file=/etc/kubernetes/pki/front-proxy-ca.crt
- --requestheader-extra-headers-prefix=X-Remote-Extra-
- --requestheader-group-headers=X-Remote-Group
- --requestheader-username-headers=X-Remote-User
- --secure-port=6443
- --service-account-issuer=https://kubernetes.default.svc.cluster.local
- --service-account-key-file=/etc/kubernetes/pki/sa.pub
- --service-account-signing-key-file=/etc/kubernetes/pki/sa.key
- --service-cluster-ip-range=10.96.0.0/12
- --tls-cert-file=/etc/kubernetes/pki/apiserver.crt
- --tls-private-key-file=/etc/kubernetes/pki/apiserver.key
image: registry.k8s.io/kube-apiserver:v1.28.5
imagePullPolicy: IfNotPresent
livenessProbe:
failureThreshold: 8
httpGet:
host: 10.0.1.28
path: /livez
port: 6443
scheme: HTTPS
initialDelaySeconds: 10
periodSeconds: 10
timeoutSeconds: 15
name: kube-apiserver
readinessProbe:
failureThreshold: 3
httpGet:
host: 10.0.1.28
path: /readyz
port: 6443
scheme: HTTPS
periodSeconds: 1
timeoutSeconds: 15
resources:
requests:
cpu: 250m
startupProbe:
failureThreshold: 24
httpGet:
host: 10.0.1.28
path: /livez
port: 6443
scheme: HTTPS
initialDelaySeconds: 10
periodSeconds: 10
timeoutSeconds: 15
volumeMounts:
- mountPath: /etc/ssl/certs
name: ca-certs
readOnly: true
- mountPath: /etc/ca-certificates
name: etc-ca-certificates
readOnly: true
- mountPath: /etc/kubernetes/pki
name: k8s-certs
readOnly: true
- mountPath: /usr/local/share/ca-certificates
name: usr-local-share-ca-certificates
readOnly: true
- mountPath: /usr/share/ca-certificates
name: usr-share-ca-certificates
readOnly: true
hostNetwork: true
priority: 2000001000
priorityClassName: system-node-critical
securityContext:
seccompProfile:
type: RuntimeDefault
volumes:
- hostPath:
path: /etc/ssl/certs
type: DirectoryOrCreate
name: ca-certs
- hostPath:
path: /etc/ca-certificates
type: DirectoryOrCreate
name: etc-ca-certificates
- hostPath:
path: /etc/kubernetes/pki
type: DirectoryOrCreate
name: k8s-certs
- hostPath:
path: /usr/local/share/ca-certificates
type: DirectoryOrCreate
name: usr-local-share-ca-certificates
- hostPath:
path: /usr/share/ca-certificates
type: DirectoryOrCreate
name: usr-share-ca-certificates
status: {}
kube-controller-manager.yaml
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
labels:
component: kube-controller-manager
tier: control-plane
name: kube-controller-manager
namespace: kube-system
spec:
containers:
- command:
- kube-controller-manager
- --allocate-node-cidrs=true
- --authentication-kubeconfig=/etc/kubernetes/controller-manager.conf
- --authorization-kubeconfig=/etc/kubernetes/controller-manager.conf
- --bind-address=127.0.0.1
- --client-ca-file=/etc/kubernetes/pki/ca.crt
- --cluster-cidr=172.16.0.0/16
- --cluster-name=kubernetes
- --cluster-signing-cert-file=/etc/kubernetes/pki/ca.crt
- --cluster-signing-key-file=/etc/kubernetes/pki/ca.key
- --controllers=*,bootstrapsigner,tokencleaner
- --kubeconfig=/etc/kubernetes/controller-manager.conf
- --leader-elect=true
- --requestheader-client-ca-file=/etc/kubernetes/pki/front-proxy-ca.crt
- --root-ca-file=/etc/kubernetes/pki/ca.crt
- --service-account-private-key-file=/etc/kubernetes/pki/sa.key
- --service-cluster-ip-range=10.96.0.0/12
- --use-service-account-credentials=true
image: registry.k8s.io/kube-controller-manager:v1.28.5
imagePullPolicy: IfNotPresent
livenessProbe:
failureThreshold: 8
httpGet:
host: 127.0.0.1
path: /healthz
port: 10257
scheme: HTTPS
initialDelaySeconds: 10
periodSeconds: 10
timeoutSeconds: 15
name: kube-controller-manager
resources:
requests:
cpu: 200m
startupProbe:
failureThreshold: 24
httpGet:
host: 127.0.0.1
path: /healthz
port: 10257
scheme: HTTPS
initialDelaySeconds: 10
periodSeconds: 10
timeoutSeconds: 15
volumeMounts:
- mountPath: /etc/ssl/certs
name: ca-certs
readOnly: true
- mountPath: /etc/ca-certificates
name: etc-ca-certificates
readOnly: true
- mountPath: /usr/libexec/kubernetes/kubelet-plugins/volume/exec
name: flexvolume-dir
- mountPath: /etc/kubernetes/pki
name: k8s-certs
readOnly: true
- mountPath: /etc/kubernetes/controller-manager.conf
name: kubeconfig
readOnly: true
- mountPath: /usr/local/share/ca-certificates
name: usr-local-share-ca-certificates
readOnly: true
- mountPath: /usr/share/ca-certificates
name: usr-share-ca-certificates
readOnly: true
hostNetwork: true
priority: 2000001000
priorityClassName: system-node-critical
securityContext:
seccompProfile:
type: RuntimeDefault
volumes:
- hostPath:
path: /etc/ssl/certs
type: DirectoryOrCreate
name: ca-certs
- hostPath:
path: /etc/ca-certificates
type: DirectoryOrCreate
name: etc-ca-certificates
- hostPath:
path: /usr/libexec/kubernetes/kubelet-plugins/volume/exec
type: DirectoryOrCreate
name: flexvolume-dir
- hostPath:
path: /etc/kubernetes/pki
type: DirectoryOrCreate
name: k8s-certs
- hostPath:
path: /etc/kubernetes/controller-manager.conf
type: FileOrCreate
name: kubeconfig
- hostPath:
path: /usr/local/share/ca-certificates
type: DirectoryOrCreate
name: usr-local-share-ca-certificates
- hostPath:
path: /usr/share/ca-certificates
type: DirectoryOrCreate
name: usr-share-ca-certificates
status: {}
kube-scheduler.yaml
apiVersion: v1
kind: Pod
metadata:
creationTimestamp: null
labels:
component: kube-scheduler
tier: control-plane
name: kube-scheduler
namespace: kube-system
spec:
containers:
- command:
- kube-scheduler
- --authentication-kubeconfig=/etc/kubernetes/scheduler.conf
- --authorization-kubeconfig=/etc/kubernetes/scheduler.conf
- --bind-address=127.0.0.1
- --kubeconfig=/etc/kubernetes/scheduler.conf
- --leader-elect=true
image: registry.k8s.io/kube-scheduler:v1.28.5
imagePullPolicy: IfNotPresent
livenessProbe:
failureThreshold: 8
httpGet:
host: 127.0.0.1
path: /healthz
port: 10259
scheme: HTTPS
initialDelaySeconds: 10
periodSeconds: 10
timeoutSeconds: 15
name: kube-scheduler
resources:
requests:
cpu: 100m
startupProbe:
failureThreshold: 24
httpGet:
host: 127.0.0.1
path: /healthz
port: 10259
scheme: HTTPS
initialDelaySeconds: 10
periodSeconds: 10
timeoutSeconds: 15
volumeMounts:
- mountPath: /etc/kubernetes/scheduler.conf
name: kubeconfig
readOnly: true
hostNetwork: true
priority: 2000001000
priorityClassName: system-node-critical
securityContext:
seccompProfile:
type: RuntimeDefault
volumes:
- hostPath:
path: /etc/kubernetes/scheduler.conf
type: FileOrCreate
name: kubeconfig
status: {}